Cyber Security Is Not Optional
Providing Innovative Security Solutions, Consultancy and Training Services
Working closely with customers to achieve success.
OUR STORY
Founded in 2010, Cystack is now the leading information security consultancy firm in Palestine. We understand the need to protect the confidentiality, integrity and availability of our customer's organizational assets. With continuous evolution of threats across the organization, Cystack understands the importance of continuous visibility and threat hunting. Cystack brings top information security professionals to the market.
The team at Cystack is highly qualified with over 30+ years of experience within the fields of IT and information security. The Team holds some of the world’s top IT and information security qualifications and certifications. Understanding our client’s needs and customizing solutions to fit those needs is our competitive advantage that sets us apart. Cystack's team is continuously engaged is securing some of the most complex infrastructures.
CONSULTANCY
The Power of working together; Cystack understands the importance of working closely with the customer to achieve success.
Cystack provides a number of consultancy services that help our customers protect their organizations and provide better services to their employees and customers.
Cystack offers comprehensive consulting and professional services that help our customers define their security strategies and implement solutions to control risks and achieve business objectives. Cystack master consulting services provide our customers with end-to-end Security coverage.
- Network Security Architecture Review
- Security Baseline Development
- Web Application Security.
- ISO27001 Gap Analysis and Certification
- Security Operation Center (SOC) Assessment
- Datacenter Security Assessment
- Data and Asset Classification
- Network and Web Applications Penetration Testing
- Physical Security Review
- Malware Analysis and Forensics Investigations
- Dark Web Monitoring
- Security Configuration Review
- Vulnerability Assessment and Management Programs
- PCI-DSS Gap Analysis and Certification
- Security Operation Center (SOC) Implementation
- Breach Readiness and Advanced Threat Protection
- Information Security Policy & Procedures Development
- Data Leakage Prevention.
- Incident Handling and Adaptive Response.
- Database Security Audits
- Mobile Application PenTesting
- Attack Surface Management
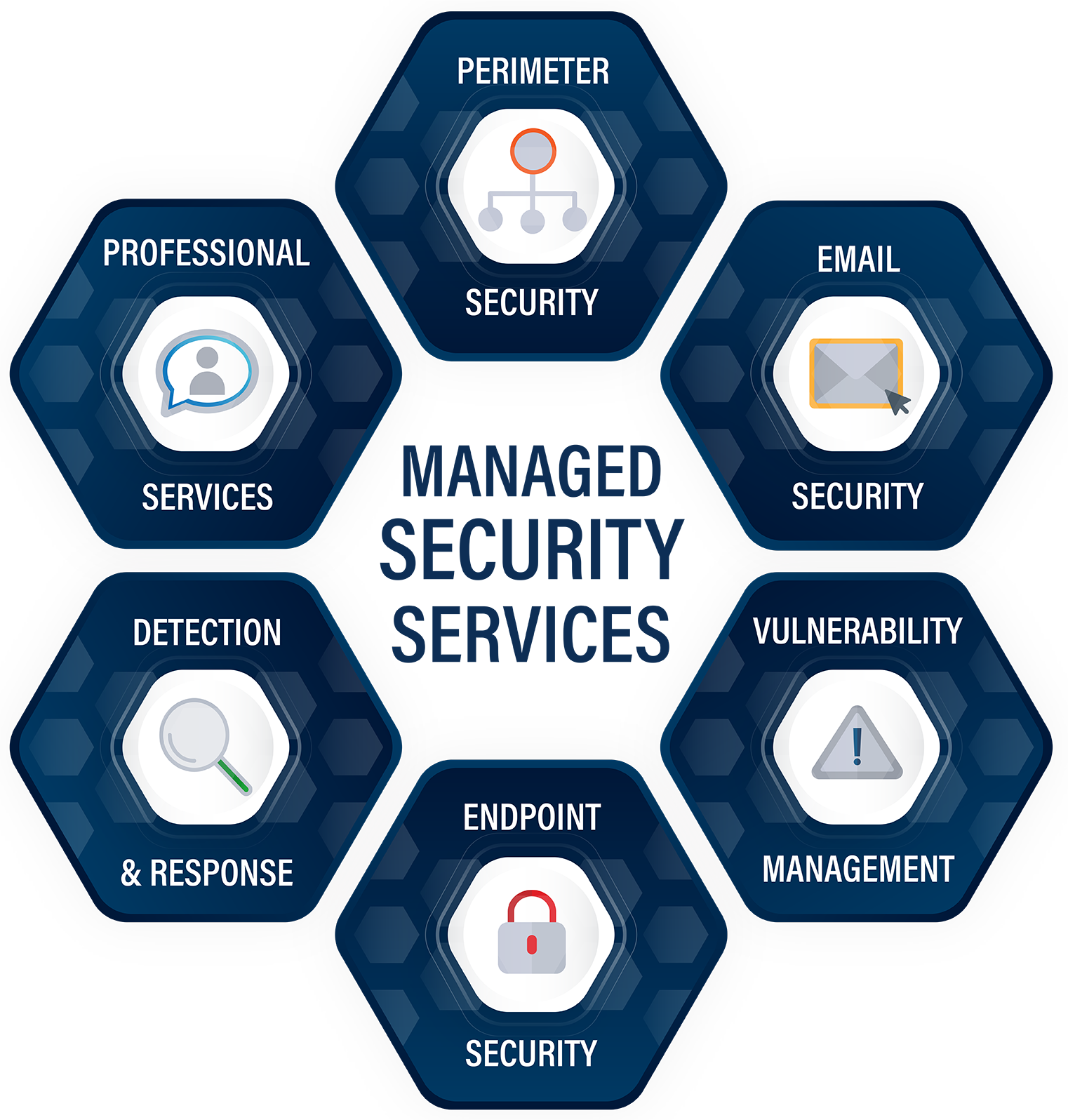
MANAGED SERVICES
- Web Application Firewall
- SIEM Threat Detection
- Network Security Management
- Security Opration Center
- Secure DNS
- Vulnerability Scanning
- Vulnerability Management
- PCI Approved Scanning Vendor
- Static Code Analysis
- Web Application Scanning
SOLUTIONS
CYSTACK is an innovative solutions provider that understands the importance of synergy in our customer’s infrastructure. CYSTACK partners with the top vendors in the local and international market and makes it a priority to provide best-in-class solutions. Some of our solutions include:
- PERIMETER AND DATACENTER FIREWALLS
- WEB APPLICATION SECURITY
- DATA SECURITY
- INTRUSION DETECTION & PREVENTION
- MALWARE PROTECTION
- SECURE REMOTE ACCESS
- AUTHENTICATION, AUTHORIZATION AND ACCOUNTABILITY
- DATA LEAKAGE PREVENTION
- DATABASE SECURITY
Latest News From Blog
CYSTACK Blogs